Logic Apps are amazingly powerful in what can be accomplished, and have a very low barrier to entry with their code-less approach, however care needs to be take to ensure security best practices are followed.
This is the first in what I hope to make a series of security tips for using Logic Apps in Azure, outlining the steps to store secrets in an Azure Key Vault and use them from your Logic App.
The scenario
In this scenario I’m creating a Logic App to read user data from the Microsoft Graph API, and will demonstrate how to retrieve the application registration client secret from an Azure Key Vault.
Scenario steps
- Create an app registration
- Enable Managed Identity on the Logic App
- Create the key vault
- Add the secret to the Key Vault
- Grant the Logic app permissions to the Key Vault
- Update the Logic App to use the Key Vault
- Final test
Create an app registration
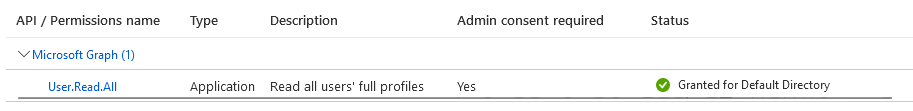
For this scenario I’ve created an Application registration in Azure AD with User.Read.All permissions, to allow it to read user data from Azure AD.
Additionally I’ve configured it with a client secret.
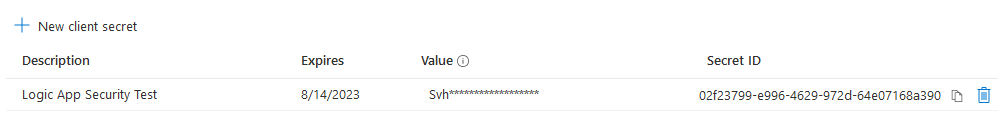
Note: Microsoft best practice recommends using application certificates rather than secrets, however I’m using secrets for the purpose of this demo as they are simpler. In a future post I’ll outline the approach for using certificates.
Creating the Logic App
For simplicity in this demo I’m creating a Consumption Logic App.
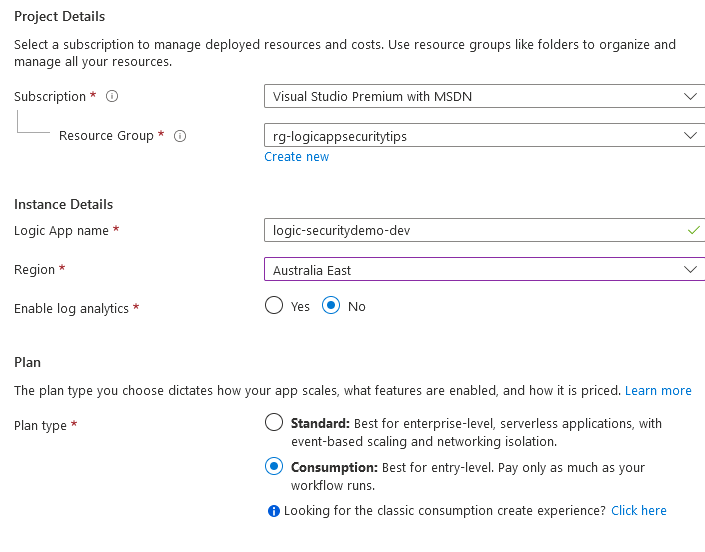
When prompted I’m creating it with a Recurrence trigger, and to minimise the consumption of the Logic App, I’m setting it to run by default every 3 months (rather than every 3 minutes).
I’ve then created a HTTP activity that is making a simple Graph API call to get all users, and the authentication has been configured using Active Directory OAuth where the client credentials are stored as Parameters in the Logic App.
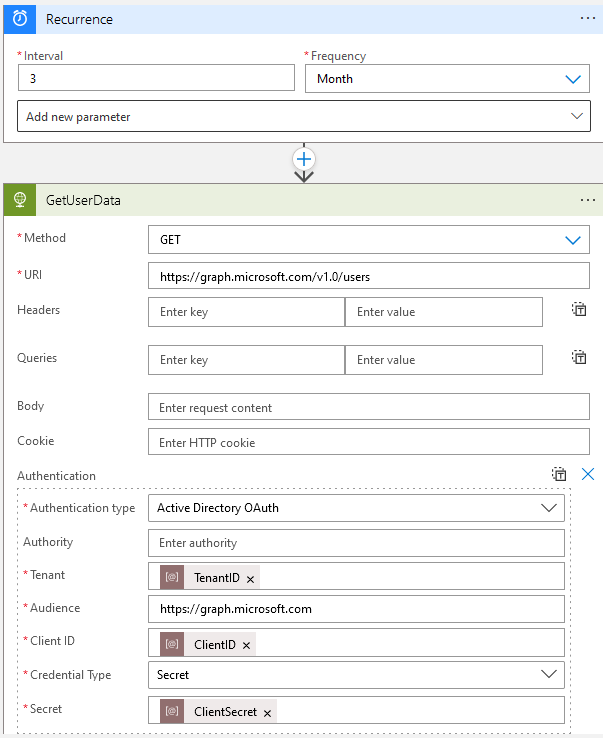
This is a bad approach for security best practice, so we need to modify the Logic App to store the credentials securely.
Enable Managed Identity on the Logic App
The first thing we need to do on the Logic App is enable a managed identity. This managed identity allows the Logic App to access resources within Azure, and in our case we will use this to securely provide access to the Key Vault we will soon create.
To do this from the Logic App settings menu select Identity.
Then under System assigned, change the Status to On and click Save (confirming Yes for any prompts that appear).
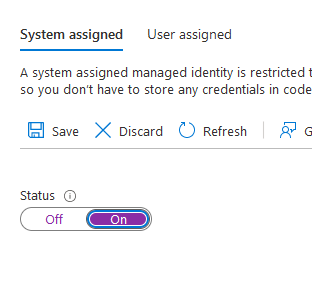
It’s possible to use User assigned managed identities also, which allows many components in Azure (such as many Logic Apps) to share the same identity. For simplicity and to demonstrate the approach, we’re just going to use a System assigned identity in this demo.
Create the key vault
Next from the Azure Marketplace Create a new Key Vault.

For this demo I’m just creating a Standard Key Vault with no special settings.
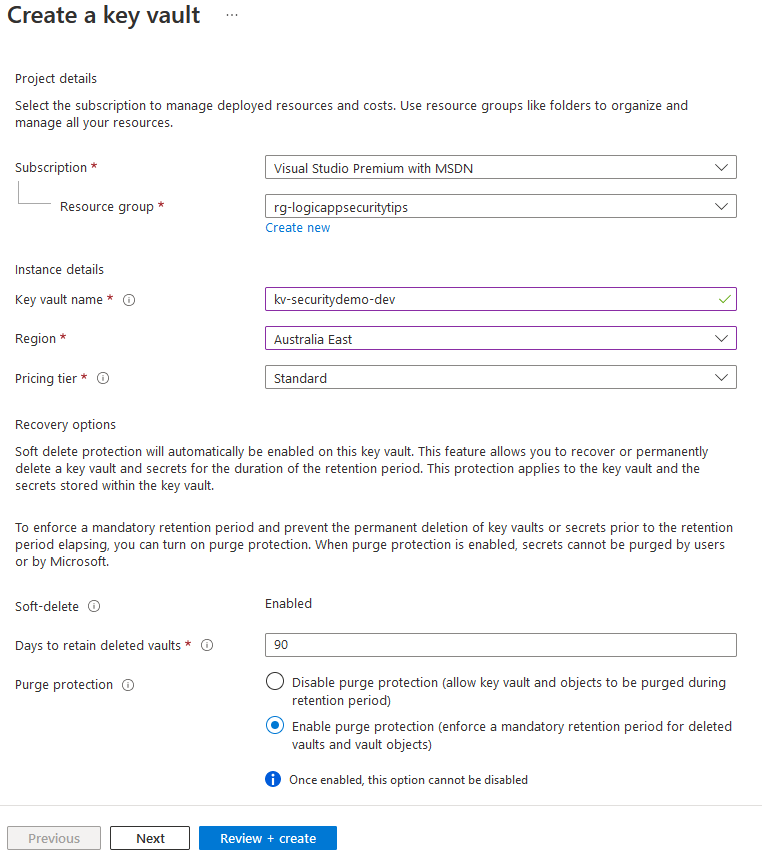
Add the secret to the Key Vault
Now that we’ve created a Key Vault we can start adding credentials. In this case from the Objects menu select Secrets. (You can also store Certificates and Keys if needed)
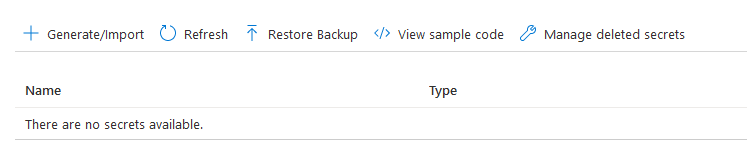
From the Secrets screen click Generate/Import.
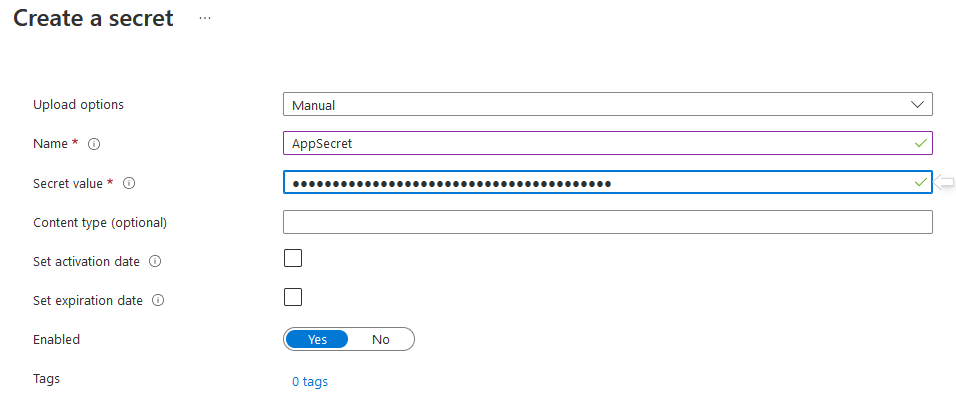
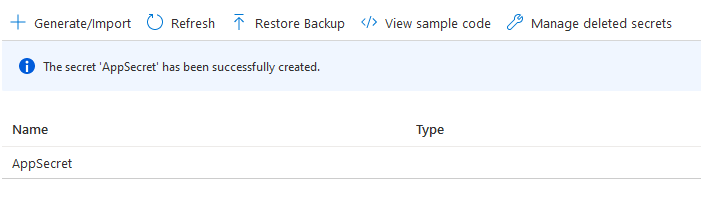
Then give the Secret an appropriate name (e.g. AppSecret) and enter the Client Secret as the Secret value, and click Create.
Once its created you can now see the secret appear in the list of secrets within the Key Vault.
Grant the Logic app permissions to the Key Vault
We now have a Key Vault with a secret, however the Logic App has no permissions to access the Key Vault. We can fix this by creating an Acess policy – select Access policies from the key vault menu.
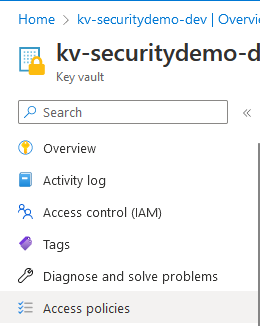
Then click Create
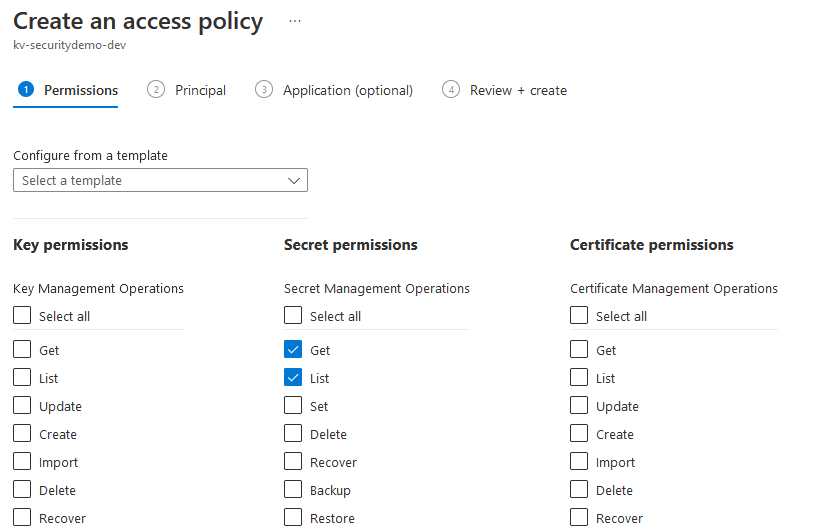
First you need to configure the permissions the Logic App needs – in this case I’m only going to provide it the following Secret permissions, then click Next
- Get – allows it to read secrets from the Key Vault
- List – allows it to see what secrets are stored in the Key Vault
Then you need to select the Logic App Principal to provide it permissions to the Key Vault. Search for it by the name of the Logic App then select it and click Next.
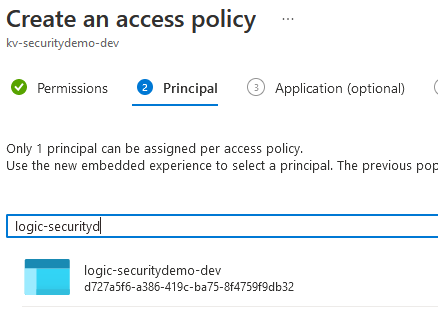
Follow the prompts to finalise creating the access policy, and it should then appear in the list of access policies.

Update the Logic App to use the Key Vault
Now that the Logic App has permissions to access the Key Vault, we can add an activity to get the Logic App to read the Client Secret from the Key Vault. First add an action after the recurrence trigger and before the GetUserData activity where we need to use the secret.
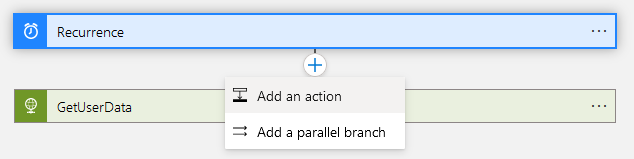
Search for the Get secret activity of the Azure Key Vault connector.
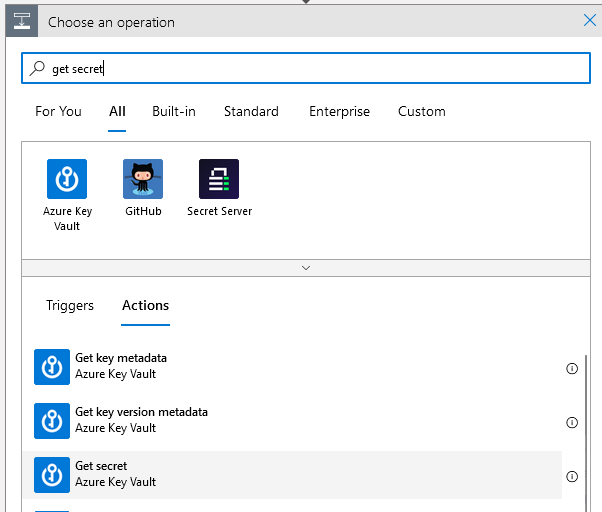
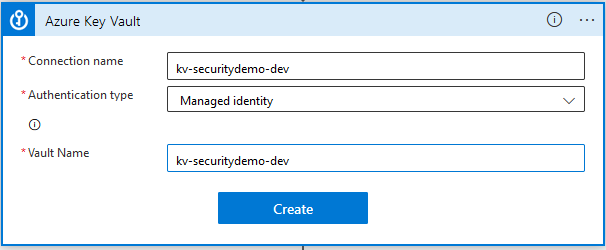
Then enter a connection name (I’ve just used the name of the Key Vault), and for the Authentication type select Managed identity.
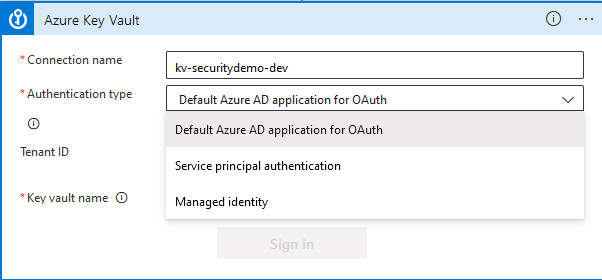
Then enter the name of the Key vault you created, and click Create.
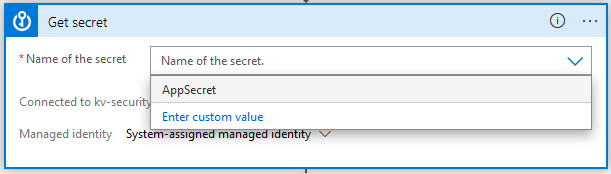
You will now see the list of secrets in the Key Vault, so select the one we created earlier named AppSecret. Note: This is where the List permission on the Key Vault is useful, if you don’t grant the List permission you have to enter the name of the secret manually.
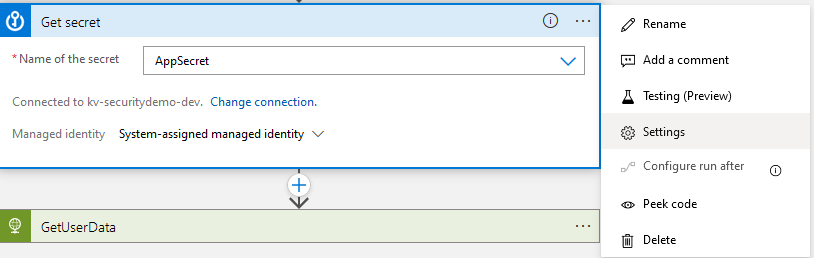
To further improve the security select Settings from the advanced settings menu (with the 3 dots).
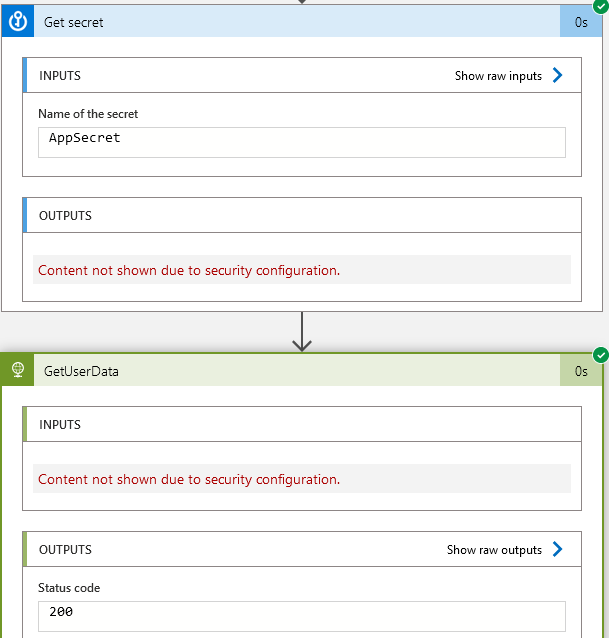
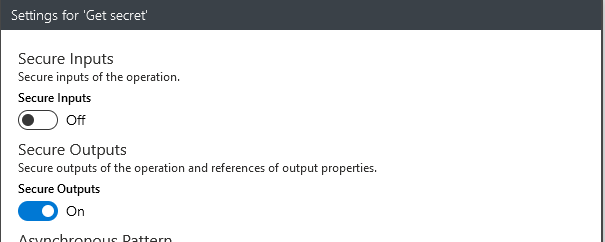
Turn Secure Outputs On. This means the secrets read from the Key Vault won’t be visible in the Logic App execution logs.
Now we can update the GetUserData activity to use the value of the secret from the Key Vault activity.

Make sure you save the Logic App changes at this point.
Final test
If you now run the Logic App it should read the secret from the Key Vault, and hide it from the logs.
Note: If you previously had the secret stored as a parameter (or hard coded), you should make sure its been removed from the Logic App.