Windows Defender Application Control (WDAC) is an application control system integrated into Windows 10/11 and is used within Enterprise to whitelist trusted applications, allowing them to run, and blocking either unauthorised or potentially malicious software.
When confirming the deployment of WDAC policies or troubleshooting issues with devices it is sometimes necessary to confirm what state the device is in, (enforcement or audit) and what policy files have been applied to a device.
Sentinel
It is possible to through a KQL query (such as the one below) in Sentinel to view policy load events. These are events where a WDAC policy has been loaded or refreshed on a device.
DeviceEvents
| where Timestamp > ago(7d)
and ActionType == "AppControlCodeIntegrityPolicyLoaded"
| project Timestamp, DeviceNameWhilst this is useful it may not always provide the full picture for the exact state of a device. Which is where PowerShell can be useful.
PowerShell
Using PowerShell it’s possible to provide some additional information and context on the state of WDAC on a device. There are two useful pieces of information:
- The device enforcement mode (displayed in msinfo32)
- The policy files that are present on a device (stored in C:\Windows\System32\CodeIntegrity\CiPolicies\Active for unsigned policies at least).
The Get-WdacStatus.ps1 script can be used to display both pieces of information for a device, and running this remotely on a user’s device can be useful in confirming the exact state of a device.
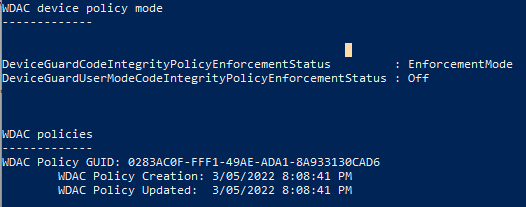
It will display the GUID of each WDAC Policy on the device, in addition to when the policy was created and last updated on the device. The GUID would need to be correlated back to the WDAC policy definition files.